![]()
One of important security issues in an organization – especially in the financial sector – is to protect the access to particular systems from unauthorized persons. Plus: to provide such access to those who should have it.
Quantitative (system-related) and qualitative (privilege-related) access should closely reflect the role and responsibilities of a particular person in an organization. Granting and revoking rights should be carried out with the use of automated mechanisms ensuring the accountability of decisions at particular levels of acceptance (workflow).
The resource access system should also manage individual user sessions and enable their supervision. Moreover, the system should offer support for the Single Sign-On, thanks to which a correctly verified user identity would allow the user to access many domain resources without re-verifying them.
When a user tries to log in to a system containing sensitive data or data being a company’s strategic resource, the mechanisms in place should verify whether the user has proper access rights. It should also ask the user for additional authentication, using another factor (e.g. mobile or hardware token, biometrics, etc.), in line with the security paradigm that requires the use of at least 2 out of 3 elements: to be, to have and to know.
All this, however, is not just a dream – such capabilities are provided by identity and access management systems as is Comarch IAM. In the past, due to its complexity and implementation difficulties, the solution was reserved only for large companies. Currently, IAM class systems are also available for smaller enterprises which can choose between on-premises, private cloud or global cloud implementation models. This diverse offer allows for adapting to different business models and needs and expectations related to the way of data processing in the organization.
Imagine John and Alice. John has just joined Chramoc Ltd as a production engineer. He will need to have access to engineering systems, employee systems and payroll systems. Alice worked as a customer advisor to the company and has now been promoted to HR. As a result, she will lose access to advisory systems and gain access to detailed information about employees and the remuneration system.
Both of them will log in to the employee systems with a login and password. In addition, John will need to log in with a software token to access the payroll system. To access the employee information system and the payroll system, Alice will need to use a hardware token.
Finally, there is Gregory, who is a client of the company and would like to check the status of his order in the client portal. Each of these people would like to get into the company’s ecosystem, but each of them needs access to different systems, and even if they overlap, a different authorization level is needed in each case. The whole situation is illustrated in the following figure.
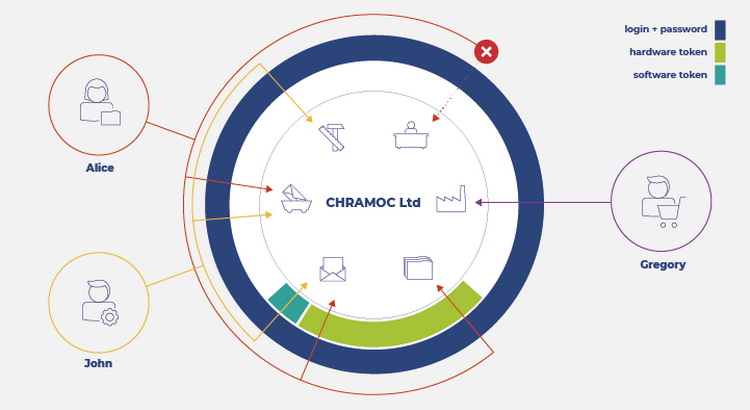
We can also imagine that Alice or John go on vacation and periodically delegate their rights to other employees, or that Gregory would like to log in to the portal and prove his identity using another external system (Google, Facebook, etc.). All this is possible thanks to the services offered by the IAM class solution.
Moreover, the system supports the administrator and the auditor in a number of control and management tasks, such as full accountability, the ability to define a password policy, create work calendars, import and export data, generate reports, compare roles in the system, or allocate rights for conflicting roles. These and other functions enable effective protection of personal data and support compliance with various standards and regulations (e.g. GDPR).
Apart from the standard password, the use of an additional identity-confirming source (tokens, biometric certificates) enables compliance with strong customer authentication for systems of particular importance to the enterprise or user (e.g. financial, employee, or patent ones) – the so-called 2-Factor Authentication (2FA). Additionally, advanced software tokens (such as Comarch tPro Mobile), allowing for a second, independent device to confirm the order made in the system, ensure compliance with the PSD2 directive.
The situation described above would contribute to the improvement of data security in any company. At the same time – which is often not so obvious in terms of cyber security – it would also help to improve the comfort of work and allow to manage the company’s resources in a thoughtful way. This is an important step that many companies
![]()
Comarch (Thailand) Company Limited
No.3, Promphan 3 Building, Unit No.1709-1710
Ladprao Soi 3, Ladprao Rd., Chom Phon, Chatuchak
Bangkok 10900, Thailand
